How to Access iPhone or Any iOS Device in Linux.
Linux is one of the best-operating systems if evaluated from a security point of view and also there are lots of stuff that is just made for the advanced user. As a Certified Ethical Hacker, I am using this operating system from previous three years and tried lots of cool things that is not at all possible on other Operating systems. Today we are here for some basic things that most of the users don’t know about. That is using your iPhone with your Linux system. In other operating systems like Windows, we quickly do install iTunes and then connect our iPhone to the PC. But such thing is not there in the Linux Operating system as you can’t install the iTunes and just do connectivity between these two devices, So today I am here with the guide that will help you to easily generate connectivity between your Linux PC and your iOS device and that too with a very easy way that you might not found anywhere else. So follow the complete guide discussed below to proceed.Learn how to use iPhone with your Linux PC using the Wine tool that is a cross platform app that will help you to install iTunes on your Linux OS and you can sync data between your iPhone and PC.
Contents: [hide]
How to Access iPhone or Any iOS Device in Linux
The method is quite simple and easy, and you just need to install one tool that will help you to run Windows apps on your Linux PC and then you can easily install iTunes in your OS and can access the files over that. So have a look on some of the simple steps that will help you to implement this in your devices.
About Wine Tool That Your Will Be Using
Wine (originally an acronym for “Wine Is Not an Emulator“) is a compatibility layer capable of running Windows applications on several POSIX-compliant operating systems, such as Linux, Mac OS, & BSD. Instead of simulating internal Windows logic like a virtual machine or emulator, Wine translates Windows API calls into POSIX calls on-the-fly, eliminating the performance and memory penalties of other methods and allowing you to cleanly integrate Windows applications into your desktop.
Steps to Access iPhone or Any iOS Device in Linux:
- Nou have the tools that you can use to install the iTunes in your Linux PC. So firstly download it on your Linux PC from here.
- Now after downloading it, you need to install that zip file on your PC, and after installation, it will check all other requirements, and you will be installing all the other files that need this tool to run the Windows apps on your Linux PC.
- Now once this process is done, you need to download the setup of iTunes according to your Windows configuration that is withering 32 bit or 64 bit.
- Now you need to double click on the downloaded file, and you will see that installation will proceed as like in Windows, that is what this tool is known for.
- Now you just need to complete the installation process, and once it is complete, you need to simply launch the iTunes app in your Linux System and then connect your iPhone with your PC using USB data cable.
- Now wait for iTunes to detect your device and start sync data between both devices, this process can take some time so be patient and let the tool do its work.
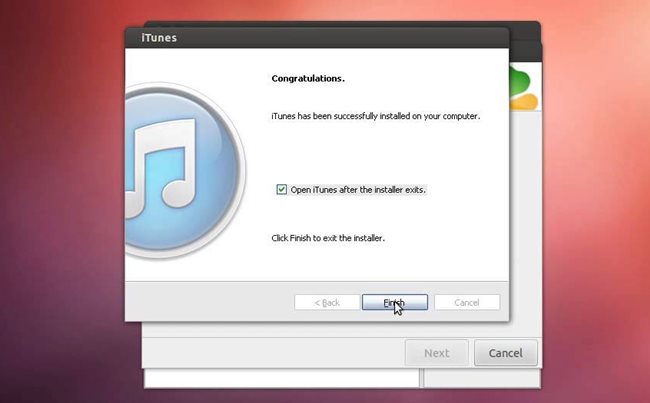
Use iPhone With Linux PC - That’s it, you are done now, you can access all your iPhone files in iTunes that got installed on your Linux System.
Other Possible Ways:
#2 Using Crossover Tool
CrossOver is a paid item that utilizes code from the free form of Wine. While it costs cash, CrossOver accomplishes a greater amount of the work for you. They test their code to guarantee that prevalent projects like Microsoft Office run well and guarantee updates won’t break them. Cross over likewise gives bolster — so if Office doesn’t run well, you have somebody to contact who will help you.
#3 Virtual Machine
You could likewise introduce iTunes in a virtual machine utilizing a program like VirtualBox or VMware and introduce Microsoft Office inside it. With Seamless Mode or Unity Mode, you could even have the Office windows show on your Linux desktop. This technique gives the best similarity, but on the other hand, it’s the heaviest — you need to run a full form of Windows out of sight. You’ll require a duplicate of Windows, for example, an old Windows XP circle you have lying around, to introduce in the virtual machine.
So above discussion was all about How to Use iPhone with Linux. Use the guide, and you can easily sync all your data between the two devices without any need for creating a server to access the files that take lots of time and mind power to setup. Simply use the app, install iTunes and enjoy all the feature of iTunes right on your Linux operating system. Hope you like the tutorial, keep on sharing with others too. Leave a comment below if you have any related queries with this tutorial as we will always be here for all our techviral users to assist.


Posted by Nagesh ;)

Comments
Post a Comment