How to Bypass and Reset the Password on Every Operating System
Passwords can be reset or bypassed on every operating system, so even if you’ve forgotten yours, there may be a way in. This also means that evildoers can likely get into your system if they have access to it—and it’s way easier than you think.
We’ll detail how to bypass the password on Windows, macOS, and Linux below, but first: if you want to protect yourself from others using this trick on you, you need to enable encryption. Your computer’s password doesn’t actually prevent access to your files, it’s just an easy way to keep not-very-determined people from using your machine. So if you really want to protect your files, you need to encrypt them—which is, thankfully, pretty easy to do.
Windows :-
There are many ways to reset a Windows password. Windows allows you to create a password reset disk that can reset your password in an approved way. Create a disk now, and you can use it if you ever need it.
If you’re using Windows 8 or 10 and you sign in with a Microsoft account, you can also reset your Microsoft account password to regain access to Windows. This is easy as long as you’ve previously associated your Microsoft account with another email address or a mobile phone number you have access to.
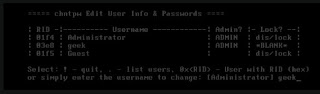
Resetting a password without an official tool is doable as well. For example, the Offline NT Password & Registry Editor works well for this. First, you’ll need to boot from a special disc or USB drive—either a live Linux system or a specialized Offline NT Password & Registry Editor boot disc. The tool can edit the Windows registry, allowing you to clear the password associated with the user account. You can then boot into Windows and log into the account without a password. Even if you’re using Windows 8 or 10 with a Microsoft account, you can always reset the password of the built-in Administrator account to gain access.
Full-disk encryption is the best way to prevent people from resetting your password and accessing your files. Make sure you don’t forget the encryption password, though! If you lose the encryption key, there is no way to get your files back—you’ll have to erase your files and reinstall Windows to regain use of the computer.
Mac OS :-
If you sign in to your Mac with an Apple ID, you can reset your Apple ID’s password to regain access to your Mac. The options on your Mac’s sign-in screen will walk you through the process. You’ll need a verification method associated with your iCloud account, like a mobile phone number.
Macs also have a built-in password reset tool available in recovery mode. You’ll need to restart your Mac by clicking the Apple menu and selecting Restart. Press and hold the Command+R keys as the computer boots and it will boot into recovery mode.
Once in recovery mode, select Terminal, type resetpassword into the terminal, and press Enter. You’ll see the Reset Password utility, which allows you to reset the password of a any user account on the Mac. You can also access this tool from a Mac OS X installation disc.
To protect yourself from this, we recommend enabling FileVault encryption (if it isn’t already—most Macs turn it on by default now). With FileVault on, you won’t be able to reset your password, so make sure you don’t forget it. If you do, you’ll have to erase your files and reinstall macOS to regain use of your Mac.
Linux OS :-
We’ll use Ubuntu as a concrete example here, but other Linux distributions work similarly. Ubuntu offers a recovery mode in its default Grub boot menu—select Advanced options for Ubuntu and select Recovery mode. You’ll see the boot menu while booting your computer—if you don’t, you can hold the Shift key as you boot and the menu will appear. You can easily boot directly to a root shell prompt from here.
This option isn’t necessary, as you can just press the e button to edit Ubuntu’s boot options and boot directly to a root shell prompt from within the main Grub menu. You’ll then be able to use the root shell to reset and change passwords on the system. If the Grub boot menu is locked and password-protected, you can still boot to Linux live media and change your password from there.
Once again, encryption would prevent your system from being accessed and modified without your encryption passphrase. We used Ubuntu as an example, but almost every Linux distribution uses Grub, and few people set a Grub password.
Chrome Book :-
Your Chromebook’s user account password is your Google account password. If you need access but forgot the password, you can just reset your Google account password on the web to regain access.
Let’s say you don’t want access to the account, but the Chromebook itself—maybe an old Google account is considered the device’s owner account. In this scenario, you can boot the Chromebook to the sign-in screen and press Ctrl+Shift+Alt+R at the same time. You’ll be prompted to factory reset your Chromebook with Powerwash. After you reset it, you can log in with another Google account and that Google account will be considered the owner account. This will erase all data on the device, but most Chromebook data is synced online.
There’s no way to gain access to a user’s files without their password on a Chromebook. Those files are encrypted by default. You can only access them if you sign in with the Google account.
Android :-
If you forget your Android’s lock screen code, you may be able to reset it. Unfortunately, this feature was removed in Android 5.0, so it won’t work on modern devices. On older devices, try an incorrect password, PIN, or pattern a few times and you may see a “Forgot password,” “Forgot PIN,” or “Forgot pattern” option. You can then regain access to your device by entering the username and password of the Google account associated with your device.
You can’t bypass the lock screen without your Google account password unless there’s a security hole you can exploit in the device. If you want to use the device, you can still perform a factory reset from recovery mode. This will set the device back to its factory state, wiping all data on it. You can then log in and set up the device with another Google account.
iPad and iPhone :-
If you forget your iPhone, iPad, or iPod Touch’s PIN or password, you can’t reset it and regain access to your device. If you forget your iOS device’s password, you’ll have to perform a factory reset. However, if you’re syncing the device to an Apple ID and you still remember your Apple ID password, all your device’s data can be restored afterward thanks to iCloud backups.
You can do this in several ways. If you’ve set up Find My iPhone, you can visit the iCloud website and erase your device from there. If you’ve backed up your device to iTunes on a computer, you can connect the device to your computer and restore your device from an iTunes backup.
If you don’t have access to Find My iPhone and you’ve never backed up the device to iTunes, you can still reset the device using recovery mode. Turn off the device, press and hold the Home button, and then connect the device’s USB cable to your computer. If it doesn’t turn on automatically, turn it on. iTunes will tell you it’s detected a device in recovery mode and allow you to restore it to factory default settings.
Passwords keep honest people honest, and they ensure people can’t gain access to your device without knowing the tricks or looking them up. But, if someone has physical access to your device and wants to bypass the password, there’s nothing you can do to stop them. Even encrypting your files will only protect your personal data—they can always wipe the encrypted data and start over fresh. However, Activation Lock can prevent a thief from using a stolen iPhone or iPad.
So, what do you think about this? Share your views in the comment box below.

We’ll detail how to bypass the password on Windows, macOS, and Linux below, but first: if you want to protect yourself from others using this trick on you, you need to enable encryption. Your computer’s password doesn’t actually prevent access to your files, it’s just an easy way to keep not-very-determined people from using your machine. So if you really want to protect your files, you need to encrypt them—which is, thankfully, pretty easy to do.
Windows :-
If you’re using Windows 8 or 10 and you sign in with a Microsoft account, you can also reset your Microsoft account password to regain access to Windows. This is easy as long as you’ve previously associated your Microsoft account with another email address or a mobile phone number you have access to.
Resetting a password without an official tool is doable as well. For example, the Offline NT Password & Registry Editor works well for this. First, you’ll need to boot from a special disc or USB drive—either a live Linux system or a specialized Offline NT Password & Registry Editor boot disc. The tool can edit the Windows registry, allowing you to clear the password associated with the user account. You can then boot into Windows and log into the account without a password. Even if you’re using Windows 8 or 10 with a Microsoft account, you can always reset the password of the built-in Administrator account to gain access.
Full-disk encryption is the best way to prevent people from resetting your password and accessing your files. Make sure you don’t forget the encryption password, though! If you lose the encryption key, there is no way to get your files back—you’ll have to erase your files and reinstall Windows to regain use of the computer.
Mac OS :-
If you sign in to your Mac with an Apple ID, you can reset your Apple ID’s password to regain access to your Mac. The options on your Mac’s sign-in screen will walk you through the process. You’ll need a verification method associated with your iCloud account, like a mobile phone number.
Macs also have a built-in password reset tool available in recovery mode. You’ll need to restart your Mac by clicking the Apple menu and selecting Restart. Press and hold the Command+R keys as the computer boots and it will boot into recovery mode.
Once in recovery mode, select Terminal, type resetpassword into the terminal, and press Enter. You’ll see the Reset Password utility, which allows you to reset the password of a any user account on the Mac. You can also access this tool from a Mac OS X installation disc.
To protect yourself from this, we recommend enabling FileVault encryption (if it isn’t already—most Macs turn it on by default now). With FileVault on, you won’t be able to reset your password, so make sure you don’t forget it. If you do, you’ll have to erase your files and reinstall macOS to regain use of your Mac.
Linux OS :-
We’ll use Ubuntu as a concrete example here, but other Linux distributions work similarly. Ubuntu offers a recovery mode in its default Grub boot menu—select Advanced options for Ubuntu and select Recovery mode. You’ll see the boot menu while booting your computer—if you don’t, you can hold the Shift key as you boot and the menu will appear. You can easily boot directly to a root shell prompt from here.
This option isn’t necessary, as you can just press the e button to edit Ubuntu’s boot options and boot directly to a root shell prompt from within the main Grub menu. You’ll then be able to use the root shell to reset and change passwords on the system. If the Grub boot menu is locked and password-protected, you can still boot to Linux live media and change your password from there.
Once again, encryption would prevent your system from being accessed and modified without your encryption passphrase. We used Ubuntu as an example, but almost every Linux distribution uses Grub, and few people set a Grub password.
Chrome Book :-
Your Chromebook’s user account password is your Google account password. If you need access but forgot the password, you can just reset your Google account password on the web to regain access.
Let’s say you don’t want access to the account, but the Chromebook itself—maybe an old Google account is considered the device’s owner account. In this scenario, you can boot the Chromebook to the sign-in screen and press Ctrl+Shift+Alt+R at the same time. You’ll be prompted to factory reset your Chromebook with Powerwash. After you reset it, you can log in with another Google account and that Google account will be considered the owner account. This will erase all data on the device, but most Chromebook data is synced online.
There’s no way to gain access to a user’s files without their password on a Chromebook. Those files are encrypted by default. You can only access them if you sign in with the Google account.
Android :-
If you forget your Android’s lock screen code, you may be able to reset it. Unfortunately, this feature was removed in Android 5.0, so it won’t work on modern devices. On older devices, try an incorrect password, PIN, or pattern a few times and you may see a “Forgot password,” “Forgot PIN,” or “Forgot pattern” option. You can then regain access to your device by entering the username and password of the Google account associated with your device.
You can’t bypass the lock screen without your Google account password unless there’s a security hole you can exploit in the device. If you want to use the device, you can still perform a factory reset from recovery mode. This will set the device back to its factory state, wiping all data on it. You can then log in and set up the device with another Google account.
iPad and iPhone :-
If you forget your iPhone, iPad, or iPod Touch’s PIN or password, you can’t reset it and regain access to your device. If you forget your iOS device’s password, you’ll have to perform a factory reset. However, if you’re syncing the device to an Apple ID and you still remember your Apple ID password, all your device’s data can be restored afterward thanks to iCloud backups.
You can do this in several ways. If you’ve set up Find My iPhone, you can visit the iCloud website and erase your device from there. If you’ve backed up your device to iTunes on a computer, you can connect the device to your computer and restore your device from an iTunes backup.
If you don’t have access to Find My iPhone and you’ve never backed up the device to iTunes, you can still reset the device using recovery mode. Turn off the device, press and hold the Home button, and then connect the device’s USB cable to your computer. If it doesn’t turn on automatically, turn it on. iTunes will tell you it’s detected a device in recovery mode and allow you to restore it to factory default settings.
Passwords keep honest people honest, and they ensure people can’t gain access to your device without knowing the tricks or looking them up. But, if someone has physical access to your device and wants to bypass the password, there’s nothing you can do to stop them. Even encrypting your files will only protect your personal data—they can always wipe the encrypted data and start over fresh. However, Activation Lock can prevent a thief from using a stolen iPhone or iPad.
So, what do you think about this? Share your views in the comment box below.

Posted by Nagesh ;)






Comments
Post a Comment