How to remove the WannaCry & Wana Decryptor Ransomware
Table of Contents
- 1Who is this guide for?
- 2What is WannaCry, WannaCryptor, WNCRY, or Wana Decryptor?
- 3How to remove the WannaCry and Wana Decryptor Ransomware
- 4Is it possible to recover WNCRY files that have been encrypted by WannaCry for Free?
- 5How to Protect yourself from the WannaCry or Wana Decryptor Ransomware.
Who is this guide for?
If a user is infected with the WanaCrypt0r/Wana Decryptor Ransomware then it is important that they remove it immediately. This is because even if you are not going to pay the ransom, while the ransomware is running it will continue to encrypt new files as they are created. This guide will guide victims on how they can remove the WannaCry and Wana Decryptor 2.0 infection from their computer.
This guide, though, will not allow you to decrypt your files for free. This is currently impossible. I will provide steps that you can use to possibly recover files (slim chance unfortunately) and methods you can use to protect your computer from ransomware in the future.
We will not be going into a technical analysis of WanaCrypt0r in this guide as it is designed for the user who just wants the infection removed. If you wish to read a more technical analysis of this ransomware, you can read this article instead: WannaCry / WanaCrypt0r Technical Nose Dive.
If there is anything missing or something doesn't make sense, feel free to ask in the Wana Decryptor 2.0 / WannaCry Help & Support Topic.
What is WannaCry, WannaCryptor, WNCRY, or Wana Decryptor?
The WannaCry Ransomware is a computer infection that is designed to encrypt your files so that you are unable to open them and then demand a ransom in bitcoins to get the decryption key. When encrypting a victim's files, the ransomware will append the .WCRY and .WNCRY extension to encrypted files. WannaCry will also create ransom note named @Please_Read_Me@.txt and executables that launch the decryptor named @WanaDecryptor@.exe.
A confusing aspect about this ransomware is that there is no definitive name for it and researchers and reporters are calling it by different names. For example, the internal name given by the developer is WanaCrypt0r, lock screen displayed by the ransomware is titled Wana Decryptor 2.0, Microsoft calls it WannaCrypt in their articles, and most of the media is calling it WannaCry.
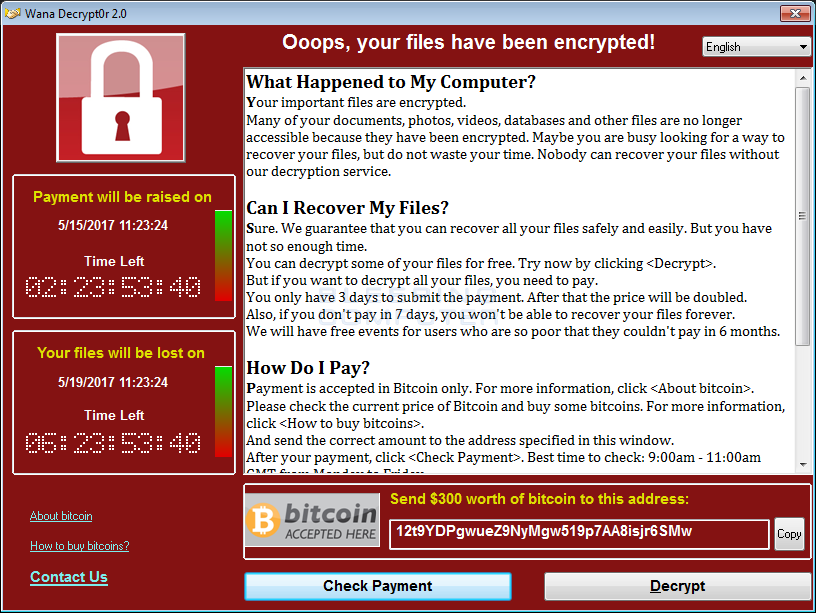
This ransomware was heavily distributed on May 12th 2017 using a alleged NSA vulnerability called EternalBlue. More information and a timeline of events can be found in the articles below:
May 12th 2017 8:40 AM: Telefonica Tells Employees to Shut Down Computers Amid Massive Ransomware Outbreak
May 12th 2017 1:07 PM: Wana Decryptor Ransomware Using NSA Exploit Leaked by Shadow Brokers Is on a Rampage
May 12th 2017 1:07 PM: Wana Decryptor Ransomware Using NSA Exploit Leaked by Shadow Brokers Is on a Rampage
May 12th 2017 5:24 PM: WannaCry / Wana Decryptor / WanaCrypt0r Info & Technical Nose Dive
May 13th 2017 4:14 AM: Wana Decryptor Ransomware Outbreak Temporarily Stopped By "Accidental Hero"
May 13th 2017 5:05 AM: Microsoft Releases Patch for Older Windows Versions to Protect Against Wana Decryptor
May 13th 2017 4:14 AM: Wana Decryptor Ransomware Outbreak Temporarily Stopped By "Accidental Hero"
May 13th 2017 5:05 AM: Microsoft Releases Patch for Older Windows Versions to Protect Against Wana Decryptor
May 14th 2017 8:00 AM: Honeypot Server Gets Infected with WannaCry Ransomware 6 Times in 90 Minutes
May 14th 2017 9:00 PM: Microsoft Exec Blames WannaCry Ransomware on NSA Vulnerability Hoarding Program
May 15th 2017 2:01 AM: With the Success of WannaCry, Imitations are Quickly In Development
May 15th 2017 1:00 PM: Someone Created a WannaCry Version That Doesn't Use a Kill Switch
How to remove the WannaCry and Wana Decryptor Ransomware
This section will provide a brief tutorial on how to remove WannaCry/Wana Decryptor using MalwareBytes and Emsisoft. While both can remove this infection on their own, as new variants are released it is better to have double-coverage during the scan. Furthermore both of these tools are free to scan and clean and you only need to purchase them if you want real-time protection or behavioral detection from ransomware.
To remove Wana Decryptor & WannaCry Ransomware, follow these steps:
1
This removal guide may appear overwhelming due to the amount of the steps and numerous programs that will be used. It was only written this way to provide clear, detailed, and easy to understand instructions that anyone can use to remove this infection for free. Before using this guide, we suggest that you read it once and download all necessary tools to your desktop. After doing so, please print this page as you may need to close your browser window or reboot your computer.
2
To terminate any programs that may interfere with the removal process we must first download the Rkill program. Rkill will search your computer for active malware infections and attempt to terminate them so that they wont interfere with the removal process. To do this, please download RKill to your desktop from the following link.

RKILL
When at the download page, click on the Download Now button labeled iExplore.exe. When you are prompted where to save it, please save it on your desktop.
3
Once it is downloaded, double-click on the iExplore.exe icon in order to automatically attempt to stop any processes associated with Sysprotector Registry Cleaner Tech Support Scam and other malware. Please be patient while the program looks for various malware programs and ends them. When it has finished, the black window will automatically close and a log file will open. Please review the log file and then close so you can continue with the next step. If you have problems running RKill, you can download the other renamed versions of RKill from the rkill download page. All of the files are renamed copies of RKill, which you can try instead. Please note that the download page will open in a new browser window or tab.
Do not reboot your computer after running RKill as the malware programs will start again.
4
Now please download Emsisoft Anti-Malware, which will scan for and remove any other adware that may have been bundled with this adware. Please download and save the Emsisoft Anti-Malware setup program to your desktop from the link below:

EMSISOFT ANTI-MALWARE
The download is fairly large, so please be patient while it downloads.
5
Once the file has been downloaded, double-click on the EmsisoftAntiMalwareSetup_bc.exe icon to start the program. If Windows Smart Screen issues an alert, please allow it to run anyway.
If the setup program displays an alert about safe mode, please click on the Yes button to continue. You should now see a dialog asking you to agree to a license agreement. Please access the agreement and click on the Install button to continue with the installation.
6
You will eventually get to a screen asking what type of license you wish to use with Emsisoft Anti-Malware.
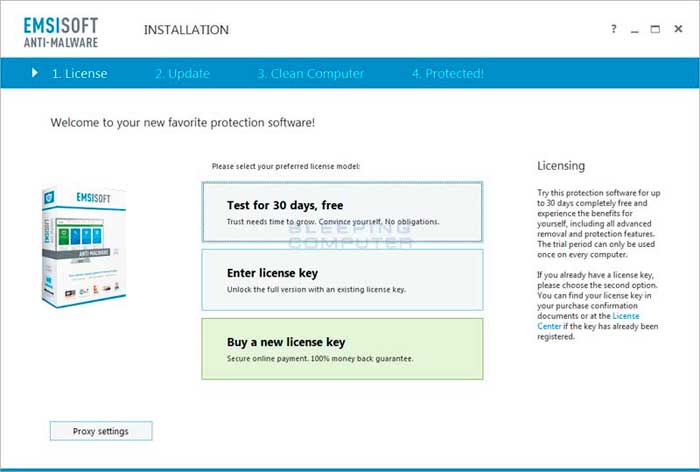
If you have an existing license key or want to buy a new license key, please select the appropriate option. Otherwise, select the Freeware or Test for 30 days, free option. If you receive an alert after clicking this button that your trial has expired, just click on the Yes button to enter freeware mode, which still allows the cleaning of infections.
7
You will now be at a screen asking if you wish to join Emsisoft's Anti-Malware network. Read the descriptions and select your choice to continue.
8
Emsisoft Anti-Malware will now begin to update it's virus detections.
Please be patient as it may take a few minutes for the updates to finish downloading.
9
When the updates are completed, you will be at a screen asking if you wish to enable PUPs detection. We strongly suggest that you select Enable PUPs Detection to protect your computer from nuisance programs such as toolbars and adware.
10
You will now be at the final installation screen. Please click on the Finish Installation button end the setup and automatically launch Emsisoft Anti-Malware.
11
Emsisoft Anti-Malware will now start and display the start screen.
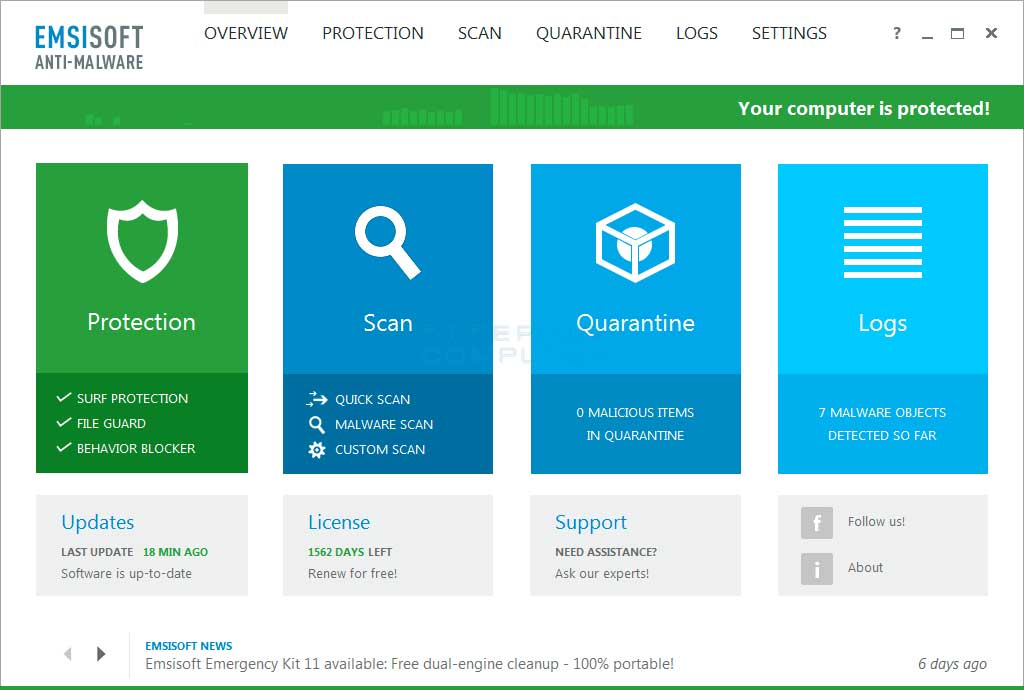
At this screen, please left-click on the Scan section.
12
You will now be at a screen asking what type of scan you would like to perform.
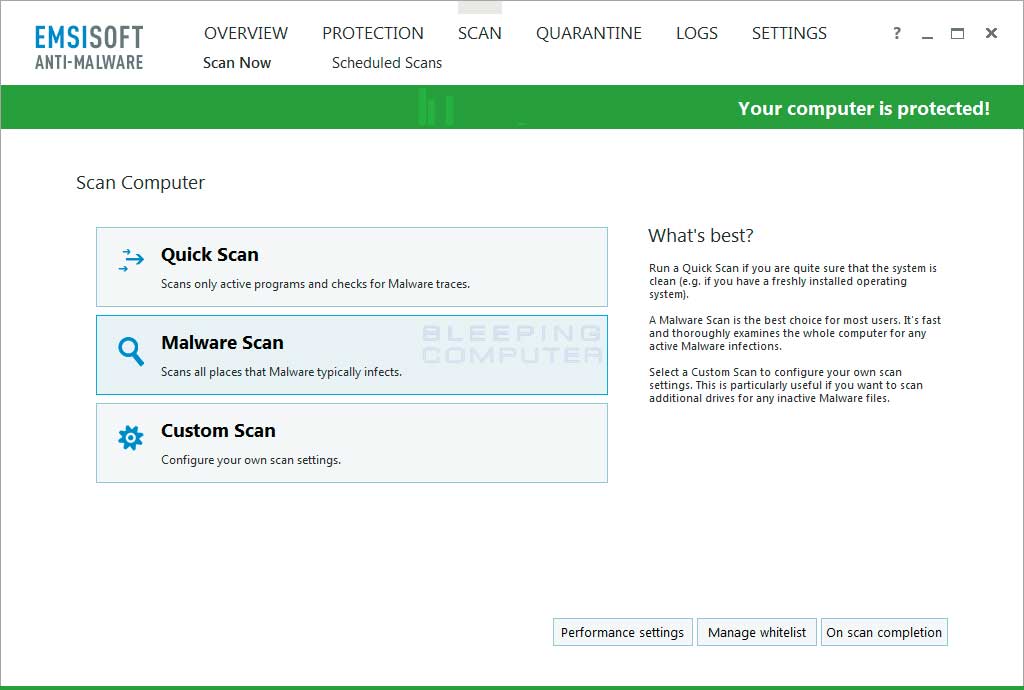
Please select the Malware Scan option to begin scanning your computer for infections. The Malware Scan option will take longer than the Quick Scan, but will also be the most thorough. As you are here to clean infections, it is worth the wait to make sure your computer is properly scanned.
13
Emsisoft Anti-Malware will now start to scan your computer for rootkits and malware. Please note that the detected infections in the image below may be different than what this guide is for.
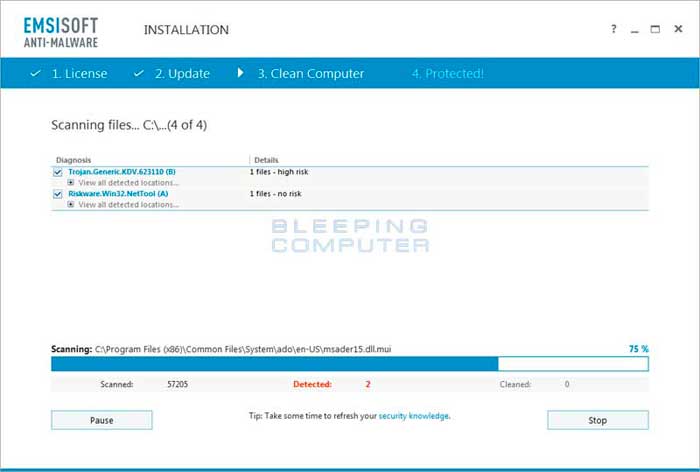
Please be patient while Emsisoft Anti-Malware scans your computer.
14
When the scan has finished, the program will display the scan results that shows what infections where found. Please note, due to an updated version of Emsisoft Anti-Malware, the screenshot below may look different than the rest of the guide.
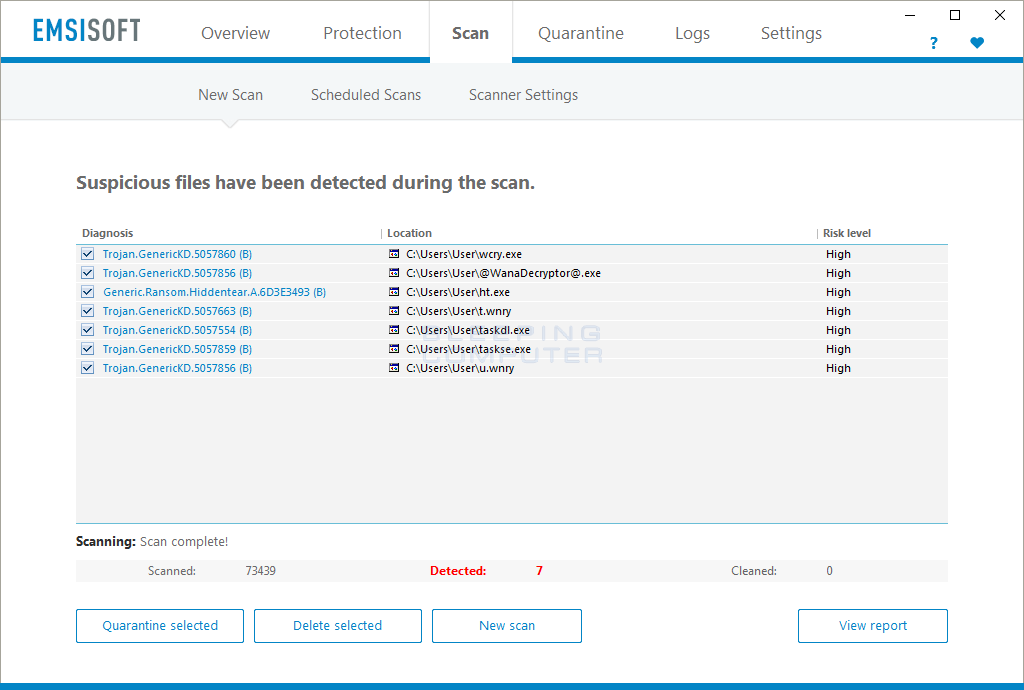
Now click on the Quarantine Selected button, which will remove the infections and place them in the program's quarantine. You will now be at the last screen of the Emsisoft Anti-Malware setup program, which you can close. If Emsisoft prompts you to reboot your computer to finish the clean up process, please allow it to do so. Otherwise you can close the program.
15
16
Once downloaded, close all programs and Windows on your computer, including this one.
17
Double-click on the icon on your desktop named mb3-setup-1878.1878-3.0.6.1469.exe. This will start the installation of MBAM onto your computer.
18
When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure you leave Launch Malwarebytes Anti-Malware checked. Then click on the Finish button. If MalwareBytes prompts you to reboot, please do not do so.
19
MBAM will now start and you will be at the main screen as shown below.
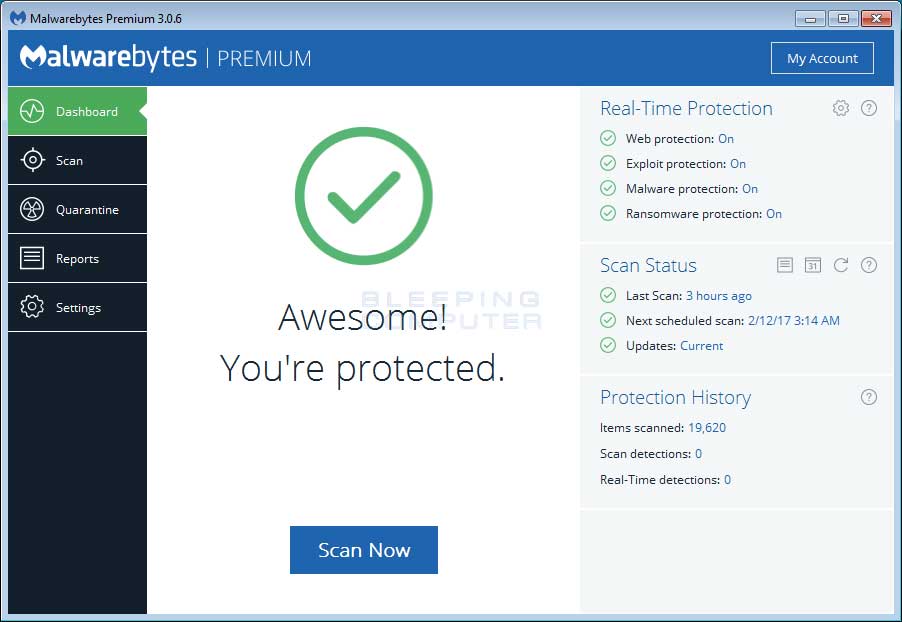
We now need to enable rootkit scanning to detect the largest amount of malware and unwanted programs that is possible with MalwareBytes. To do this, click on the Settings button on the left side of the screen and you will be brought to the general settings section.
Now click on the Protection tab at the top of the screen. You will now be shown the settings MalwareBytes will use when scanning your computer.
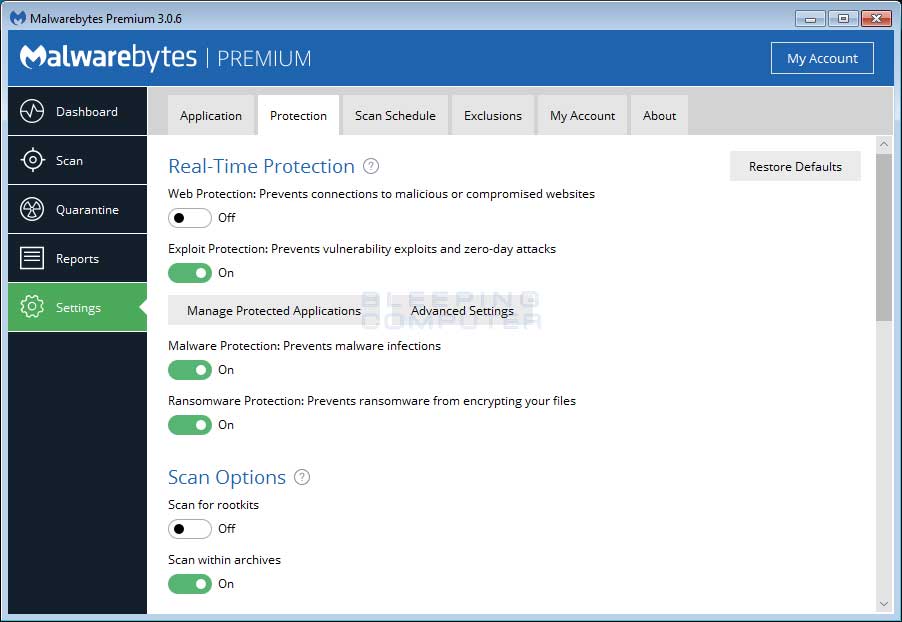
At this screen, please enable the Scan for rootkits setting by clicking on the toggle switch so it turns green.
20
Now that you have enabled rootkit scanning, click on the Scan button to go to the scan screen.
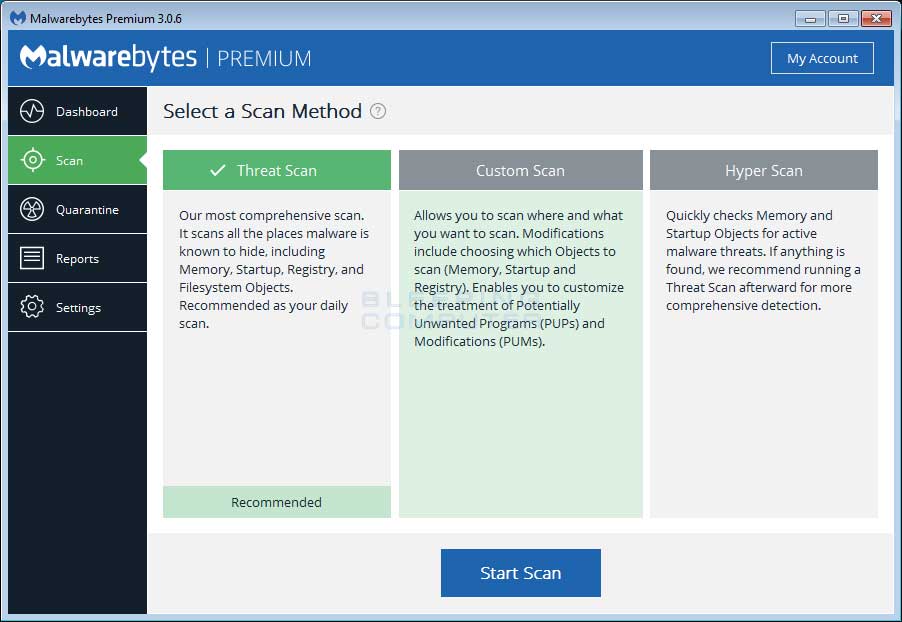
Make sure Threat Scan is selected and then click on the Start Scan button. If there is an update available for Malwarebytes it will automatically download and install it before performing the scan.
21
MBAM will now start scanning your computer for malware. This process can take quite a while, so we suggest you do something else and periodically check on the status of the scan to see when it is finished.
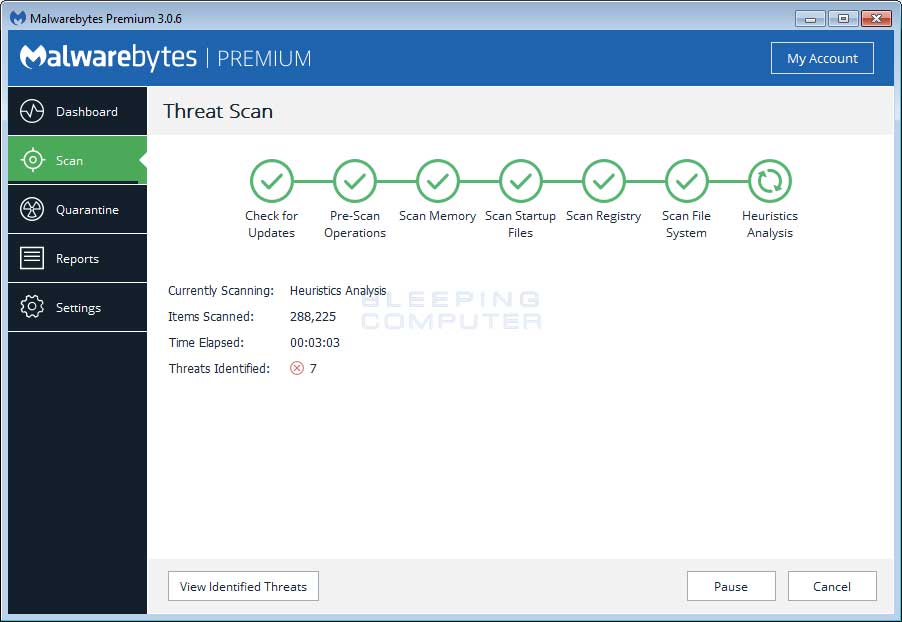
22
When MBAM is finished scanning it will display a screen that displays any malware, adware, or potentially unwanted programs that it has detected. Please note that the items found may be different than what is shown in the image below due to the guide being updated for newer versions of MBAM.
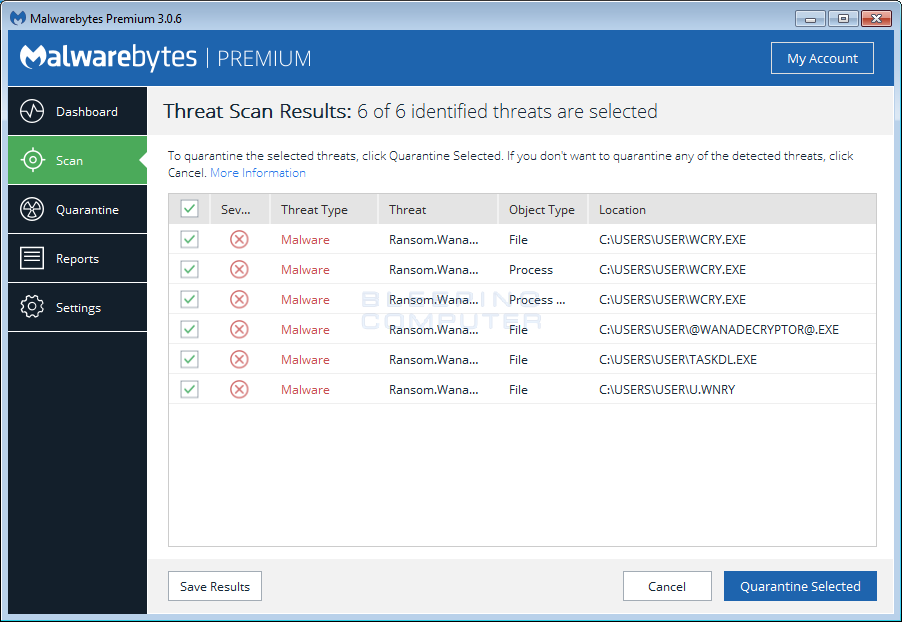
You should now click on the Remove Selected button to remove all the selected items. MBAM will now delete all of the files and registry keys and add them to the programs quarantine. When removing the files, MBAM may require a reboot in order to remove some of them. If it displays a message stating that it needs to reboot, please allow it to do so. Once your computer has rebooted, and you are logged in, please continue with the rest of the steps.
23
You can now exit the MBAM program.
Is it possible to recover WNCRY files that have been encrypted by WannaCry for Free?
Unfortunately, there is no way to decrypt WNCRY files that were encrypted by the WannaCry Ransomware for free. There may, though, be methods to restore encrypted files that were stored on Dropbox or from Shadow Volume Copies that were not removed by the ransomware for some reason.
Method 1: Restoring from Shadow Volume Copies:
If you had System Restore enabled on the computer, Windows creates shadow copy snapshots that contain copies of your files from that point of time when the system restore snapshot was created. These snapshots may allow you to restore a previous version of your files from before they had been encrypted. This method is not fool proof, though, as even though these files may not be encrypted they also may not be the latest version of the file. Please note that Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, & Windows 8.
For a detailed explanation on how to restore files from Shadow Volume Copies, you can see this tutorial: How to recover files and folders using Shadow Volume Copies.
Method 2: Restoring WNCRY files that were encrypted on DropBox folders
If you have DropBox mapped to a drive letter on an infected computer or synchronized to a folder, Wana Decryptor will attempt to encrypt the files on it. DropBox offers free versioning on all of its accounts that will allow you to restore encrypted files through their website. Unfortunately, the restoral process offered by DropBox only allows you to restore one file at a time rather than a whole folder. If you need instructions on restoring an entire folder in DropBox, please click here.
To restore a file, simply login to the DropBox web site and navigate to the folder that contains the encrypted files you wish to restore. Once you are in the folder, right-click on the encrypted file and select Previous Versions as shown in the image below.
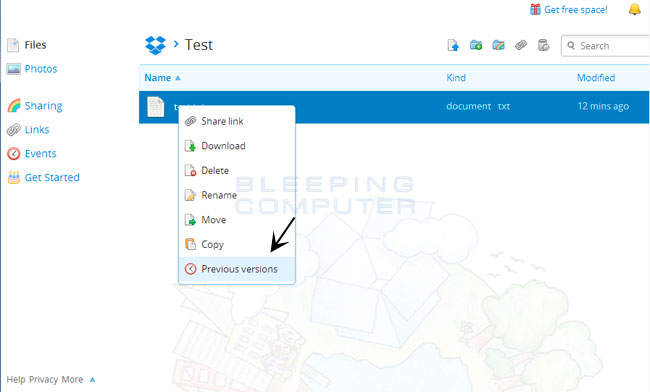
When you click on Previous versions you will be presented with a screen that shows all versions of the encrypted file.
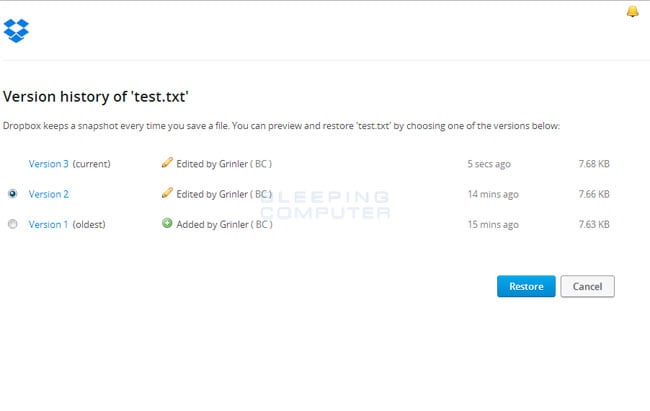
Select the version of the file you wish to restore and click on the Restore button to restore that file.
Unfortunately the process outlined above can be very time consuming if there are many folder to restore. In order to restore an entire folder of encrypted files, you can use the dropbox-restore python script located here. Please note that this script requires Python to be installed on the encrypted computer to execute the script. Instructions on how to use this script can be found in the README.md file for this project.
How to Protect yourself from the WannaCry or Wana Decryptor Ransomware.
The first thing you need to do is make sure you have all the Windows Updates installed. You need to especially install the updates discussed in MS17-010. If you are using Windows XP, Windows 8, or Windows Server 2003 then you can use this special update released by Microsfoft.
There are a few methods and utilities that we recommend in order to protect your computer from ransomware infections. Three of the methods are Emsisoft Anti-Malware, HitmanPro: Alert, and Malwarebytes Anti-Malware. The fourth option is to utilize Software Restriction Policies that prevent programs from being allowed to execute from certain locations. In full disclosure, BleepingComputer.com makes a commission off of the sales of Emsisoft Anti-Malware, HitmanPro: Alert, and Malwarebytes.
Emsisoft Anti-Malware:
Emsisoft Anti-Malware, or EAM, has a feature called behavior blocker that has a proven track record of blocking ransomware before it can start encrypting data on your computer. Unlike traditional antivirus definitions, EAM's behavior blocker examines the behavior of a process and if this behavior contains certain characteristics commonly found in malware it will prevent it from running. Using the detection method, behavior blocker detects when a process is scanning a computer for files and then attempting to encrypt them. If it discovers this behavior, it will automatically terminate the process.
When I tested Emsisoft's behavior blocker against WanaCrypt0r it was able to block it from encrypting my files.
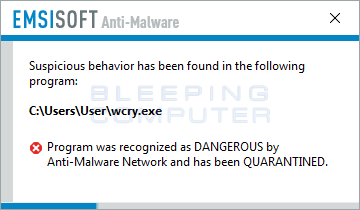
You can find more information about Emsisoft Anti-Malware and behavior blocker here: https://www.emsisoft.com/en/software/antimalware/
HitmanPro: Alert:
HitmanPro: Alert is a great program as well but is designed as a full featured anti-exploit program and is not targeted exclusively at ransomware infections. Alert provides protection from computer vulnerabilities and malware that attempts to steal your data. Unfortunately, because this program has a much broader focus it sometimes needs to be updated as new ransomware is released. As long as you stay on top of the updates, HitmanPro: Alert offers excellent protection.
You can find more information about HitmanPro: Alert here: https://www.hitmanpro.com/
Malwarebytes Anti-Malware
Malwarebytes is another program that does not rely on signatures or heuristics, but rather by detecting behavior that is consistent with what is seen in ransomware infections. You can get more information information about Malwarebytes Anti-Malware here: https://buy.malwarebytes.com/us/.
Configure Application Whitelisting:
A very secure method of preventing a ransomware, or almost any other malware, infection is to use a method called Application Whitelisting. Application whitelisting is when you lock down Windows so that all executables are denied except for those that you specifically allow to run. Since you are only allowing programs you trust to run, if you are infected the malware executable would not be able to run and thus could not infect you. For those who are interested in learning more about application whitelisting, you can view this tutorial: How to create an Application Whitelist Policy in Windows.
Use Software Restriction Policies to block executables in certain file locations:
You can use the Windows Group or Local Policy Editor to create Software Restriction Policies that block executables from running when they are located in specific file locations. For more information on how to configure Software Restriction Policies, please see these articles from MS:
The file paths that have been used by this infection and its droppers are:
C:\Users\<User>\AppData\Local\<random>.exe (Vista/7/8)
C:\Users\<User>\AppData\Local\<random>.exe (Vista/7/8)
C:\Documents and Settings\<User>\Application Data\<random>.exe (XP)
C:\Documents and Settings\<User>\Local Application Data\<random>.exe (XP)
%Temp%
C:\Windows
In order to block Locky, and other ransomware, you want to create Path Rules so that they are not allowed to execute. To create these Software Restriction Policies, you can either use the CryptoPrevent tool or add the policies manually using the Local Security Policy Editor or the Group Policy Editor. Both methods are described below.
How to use the CryptoPrevent Tool:
FoolishIT LLC was kind enough to create a free utility called CryptoPrevent that automatically adds the suggested Software Restriction Policy Path Rules listed above to your computer. This makes it very easy for anyone using Windows XP SP 2 and above to quickly add the Software Restriction Policies to your computer in order to prevent Locky, and other ransomware, from being executed in the first place. This tool is also able to set these policies in all versions of Windows, including the Home versions.
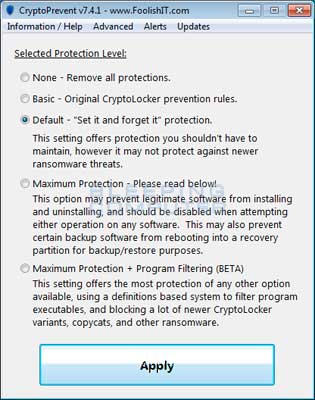
A new feature of CryptoPrevent is the option to whitelist any existing programs in %AppData% or %LocalAppData%. This is a useful feature as it will make sure the restrictions that are put in place do not affect legitimate applications that are already installed on your computer. To use this feature make sure you check the option labeled Whitelist EXEs already located in %AppData% / %LocalAppData% before you press the Block button.
You can download CryptoPrevent from the following page:
For more information on how to use the tool, please see this page:
Once you run the program, simply click on the Apply Protection button to add the default Software Restriction Policies to your computer. If you wish to customize the settings, then please review the checkboxes and change them as necessary. If CryptoPrevent causes issues running legitimate applications, then please see this section on how to enable specific applications. You can also remove the Software Restriction Policies that were added by clicking on the Undo button.


Posted by Nagesh ;)

Comments
Post a Comment